According to the US Department of Justice, “cyberstalking is using the internet, e-mail, or other electronic communications devices to stalk another person”. These types of harassment via the internet may seem harmless, but they can become dangerous. So, to protect your child against these threats, you first need to know how to spot them in their different forms. In this blog, we will talk about types of cyberstalking.
What Is Cyberstalking?
In cyberstalking, a stalker uses technology to contact and harass their victim. This causes the victim of cyberstalking to feel unsafe and scared. Cyberstalking can be similar in some points to cyberbullying. However, there are also differences: Cyberbullying can happen by cyberbullies who are the same age as the victim, while cyber-stalkers are usually adults.
Unfortunately, cyberstalking is something that’s not resolved without intervention. Statistics indicate that in 75 percent of the cases, the situations escalate without intervention.
7 Different Types of Cyberstalking
There are different types of cyberstalking, in this part, we’ve listed seven of them for you:
E-Mail Cyberstalking
Email stalking is a prevalent form, where the stalker uses email to harass or intimidate the victim. This can include sending a large number of unwanted messages, threats, or disturbing content. The stalker may create multiple email accounts to continue the harassment if blocked, making it challenging for the victim to escape the unwanted attention.
Cyberstalking through Instant Messaging and Texting
It involves using messaging apps and SMS to send persistent, unsolicited messages. This form of stalking can be particularly invasive as it often targets the victim’s mobile device, making it difficult to avoid the constant barrage of messages. Apps like WhatsApp, Facebook Messenger, and regular SMS services are common tools used in this type of cyberstalking.
Social Media Stalking
It involves the obsessive monitoring of someone’s social media activity. This form of cyberstalking typically includes repeatedly visiting someone’s profiles, liking old posts, leaving unwanted comments, and sending threatening or unsolicited messages.
Social media platforms like Facebook, Instagram, Twitter, and LinkedIn are common venues for this type of stalking. The stalker may use these platforms to gather personal information, track the victim’s activities, and attempt to establish unwanted contact.
Catfishing
Catfishing is when a stalker creates fake profiles, websites, or social media posts in the victim’s name to harm their reputation or lure others into unwanted contact with the victim. This identity theft can lead to significant personal and professional damage as the victim’s identity is misused. The stalker might also join forums and social media groups under the victim’s name to spread false information.
Monitoring and Surveillance
This type of cyberstalking involves using technology to track the victim’s online activities. This can include hacking into personal accounts, installing spyware on devices, and using GPS to track physical movements. The stalker may monitor emails, browsing history, and even live webcam feeds to gather personal information and maintain control over the victim.
Doxxing
Doxxing is a particularly malicious form of cyberstalking where the stalker publicly shares private information about the victim, such as home addresses, phone numbers, email addresses, and financial details. The intent is often to intimidate, threaten, or cause physical harm by exposing the victim to broader harassment and stalking from others.
Hijacking Webcams
Webcams can be hijacked by introducing the victim’s computer to malware-infected files. By hijacking the victim’s webcam, they can even record the daily activities of their victim and use it as harassment.
It is often seen that a combination of stalking ways is used to harass a victim.

Signs of Cyberstalking
According to KidsHealth, if you notice these signs in your teen, they might be experiencing cyberstalking:
- They spend an unusual amount of time privately online
- They receive messages, e-mails, or phone calls at strange hours
- When they are online, they act suspiciously
- They are receiving gifts from unknown people
- After being online they seem bothered, scared, upset, or crying
How to Prevent Cyberstalking
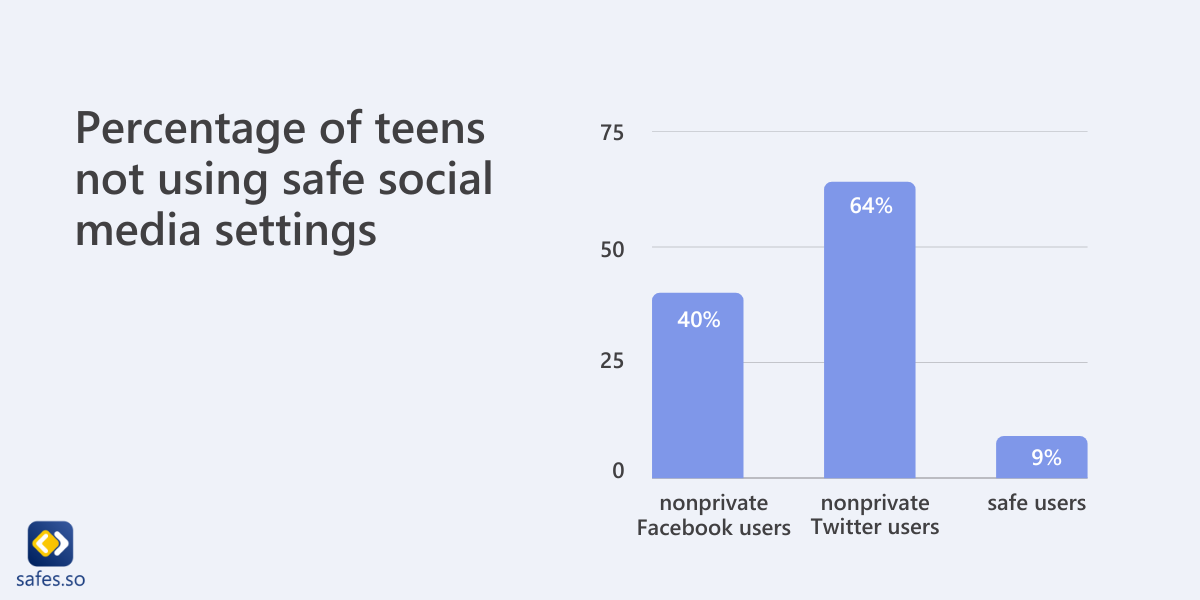
Many teens don’t take the necessary precautions to protect themselves online. According to research, 40 percent of teen Facebook users and 64 percent of young Twitter users don’t have their social media privacy settings activated. Only 9 percent of teens were “very” concerned about third parties accessing their personal information. It might not be possible to prevent cyberstalking from ever happening to your teen, but let’s go over some ways to reduce the chances of cyberstalking.
Keep Accounts Private and Secure
Most social media apps have privacy settings. These settings can hide or cover your teen’s profile from strangers. They will ask for their permission before anyone can add them as a friend. This allows only people who are intentionally added as friends to see their photos or posts.
A good habit to get your kids used to is logging out of their accounts. In case their device gets lost or stolen, nobody can access their accounts such as Instagram or e-mail.
As an additional layer of safety, it’s good to teach your child not to use his or her real name online, as well as not to share optional information such as place of residence. The fewer people have information about your child online, the less likely they are to misuse it.

Online Safety Habits
Online safety habits, like keeping their password private and changing it frequently, are important things parents have to teach their teens. Even in instances where teens trust each other, it’s never certain that the shared information will stay private after a disagreement or a breakup.
As an extra protection, you might want to consider anti-spyware software. This software detects malicious software on your teen’s device and can help you get rid of it. If spyware has already infected their device, a factory reset has to be done. To prevent all their data from being lost, it is sensible to make a backup.
Phone and Locations Should be Secure
It’s important to teach your teen how important it is to not leave their phone unattended. It only takes a few minutes for someone to install spyware without leaving a trace or hacking into social media accounts.
Another important safety measure is to enlighten your teen on keeping their geolocations and GPS turned off. It’s always better to post what was done afterward, rather than in the moment itself. When posting right at the moment with your location linked to your post, it gives cyber-stalkers enough information to find you.
Examples of Cyberstalking
Let’s read about one of the most recent cyberstalking examples from the news.
On Tuesday, January 17, 2023, a man from Ohio was sentenced to more than 12 years in prison and 15 years of supervised release after he was found guilty of, among other things, cyberstalking. The First Assistant United States Attorney Michelle M. Baeppler said: “It takes great courage for victims to come forward and report coercive behavior and predatory tactics to law enforcement, because these victims came forward, this defendant was brought to justice, a minor was prevented from further harm, and our communities and children are now safer.”
The FBI Agent in charge mentions that the defendant used to blackmail numerous victims. The stalker gained unauthorized access to his victim’s social media accounts and phone numbers. As part of a scheme, he obtained non-public images and other sensitive materials. Later he threatened his victims to make the materials public and followed this through in some cases.
As read from the example above, your teen needs to come forward if someone is cyberstalking them. This can prevent other kids from getting harassed, and the harasser will get what they deserve.
How Can Parents Help against Cyberstalking?
According to the previously mentioned information of KidsHealth, when your child is cyber-stalked you can offer help by:
Support and Comfort
In times when your child is being stalked online, it is important to offer them comfort. Getting stalked is not your child’s fault. Let them know that you will support them to get through this time. Praise your teen for talking about it, and reassure them that you’ll figure out what to do together.
Keep Records
Many cyberstalking laws require proof to prevent false accusations. It can be wise to keep screenshots or threatening messages. These can be used as evidence in later stages when you want to file a complaint with the police.
Get Help
Meeting with a therapist can help your child work through their feelings. Another option is to reach out to a counselor or mediator at school. It can also be beneficial to report it to the police so they can prosecute the stalker.
Monitor Your Child’s Social Media Use
Currently, there are apps available to monitor your child’s online internet behavior. One of these apps is Safes. This parental control app offers a lot of features to keep your kid safe online. Some of these features are:
- Content management: Content management helps parents monitor and set boundaries for content and communication accessible on children’s devices. It reports on voice calls and text messages, app installations, social media usage, suspicious photos, and alarming words.
- Detailed activity reports: This feature informs parents about their children’s device and internet usage patterns and the consumed content.
- Comprehensive profiles: The monitoring process can be simplified by creating separate profiles for every child.
Try out Safes by downloading the free app. Sign up for a free trial today!




