When spoken about bullying, most of us tend to think of bullying in school. If only bullying stopped there. But Bullies will be bullies their whole life if not properly solved at a young age. In this article, we will introduce various forms of cyberbullying and show you some examples. We will also share the experiences of some of the victims, to give you a deeper understanding of the meaning of cyberbullying.
How to prevent and stop cyberbullying?
As the Internet gained popularity and became a tool of the first century it attracted more and more participants. However, this growth also brought challenges. Cyberbullying, which refers to the repetitive use of tools to torment individuals has emerged as a global concern especially among today’s youth.
Bullying in all its forms can cause distress to its victims. Many individuals who experience cyberbullying suffer, from symptoms, like anxiety, panic attacks, and clinical depression. In some cases, it tragically leads to suicide.
Before delving into the aspects of cyberbullying and the experiences of those affected by it it is crucial to understand why people engage in behavior; According to Broadband Search, the main reasons in 2022 are:
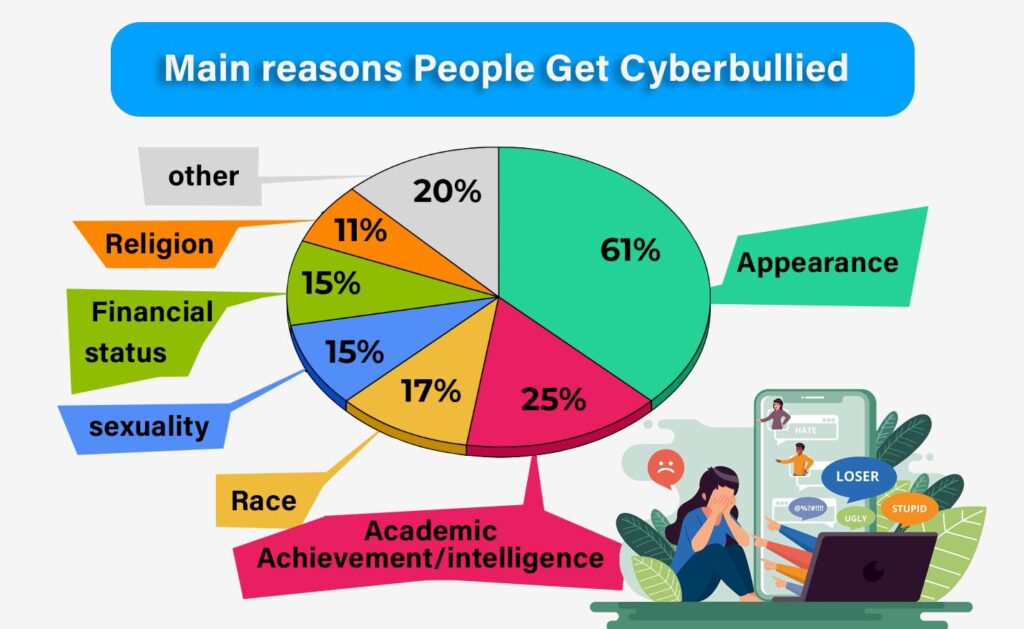
Within the context of the broader issue of cyberbullying, it’s crucial to remind your child:
- They Are Not the Problem: Their appearance, race, religion, or any other aspect of who they are does not make them the issue at hand.
- Bullies Target Differences: Cyberbullies tend to zero in on individuals who they perceive as different in some way. This could stem from a desire to exert control or because they see them as a threat.
- Their Response Matters: Regardless of the motivations behind cyberbullying, Their response is what truly counts.
In the fight against cyberbullying, it’s essential to:
- Educate Yourself: Learn about the dynamics of bullying and cyberbullying, and explore strategies to prevent and combat it.
- Seek Support: Helplines and support networks can offer valuable assistance to those affected by cyberbullying.
For more in-depth information and resources, continue reading this article. Additionally, understanding cyberbullying laws and associated penalties is crucial. Notably, law enforcement and other authorities are increasingly using the term “eCRIME” when addressing cyberbullying concerns.
The most common forms of cyberbullying
Cyberbullying manifests in various ways, but some forms are particularly prevalent in today’s digital landscape:
1. Exclusion
Have you or your child ever been left out of a group of friends? You might have seen this happen in person, or maybe even online. If someone is left out deliberately, then it’s exclusion. When somebody is uninvited to parties or left out of group conversations online, that’s exclusion.

2. Harassment
Online harassment refers to a series of repeated threatening and negative messages to someone, with the purpose of hurting them.
3. Outing/Doxing
We’ve all heard about somebody having their photos and data revealed to the public, without them even knowing until they got out.
Outing or doxing means putting out someone’s personal information (any type) with the intention of humiliating them.

4. Trickery
Many victims are “tricked” by unknown individuals to reveal their secrets, information, and parents’ debit card PIN codes. Much similar to the outing, trickery is revealing someone’s sensitive information without their consent, only with the element of deception added to it. Bullies may pose as someone they’re not, and gain their target’s trust. They then share their private information online or with third parties in order to hurt and embarrass them.
5. Cyberstalking
Sure, if somebody monitors your coming and going, and knows where do you go every day and when it’s called stalking.
But like many forms of bullying, there is an online method.
Bullies stalk and harass their victims using technology. Those who choose this method are often tech-savvy and creative and continuously send messages and torment people.
They might, for example, join the same groups and conversations as their targets, message them excessively, and create multiple fake accounts to stalk them.

6. Fraping
Fraping is using somebody else’s social network account without their permission, changing the information and comments of the account, and posting offensive material through it.
7. Masquerading
Masquerading is putting the blame for cyberbullying on somebody else. When a bully creates a profile with cyberbullying others as the main purpose. It may take a while for the victim to prove that he wasn’t the perpetrator. It is better to report the fake account as soon as possible.
8. Dissing
Dissing refers to the intention of ruining a person’s reputation and relationships by spreading false, embarrassing information about them.
9. Trolling
Trolling refers to posting comments the bully knows will hurt the victim.
This is one of the most common forms of cyberbullying. There are bullies who post insulting comments, sometimes because they think it’s funny in many comment sections.
It ranges from insulting an individual due to racial or sexual orientation differences to an argument over basic things, like which Football team is better.
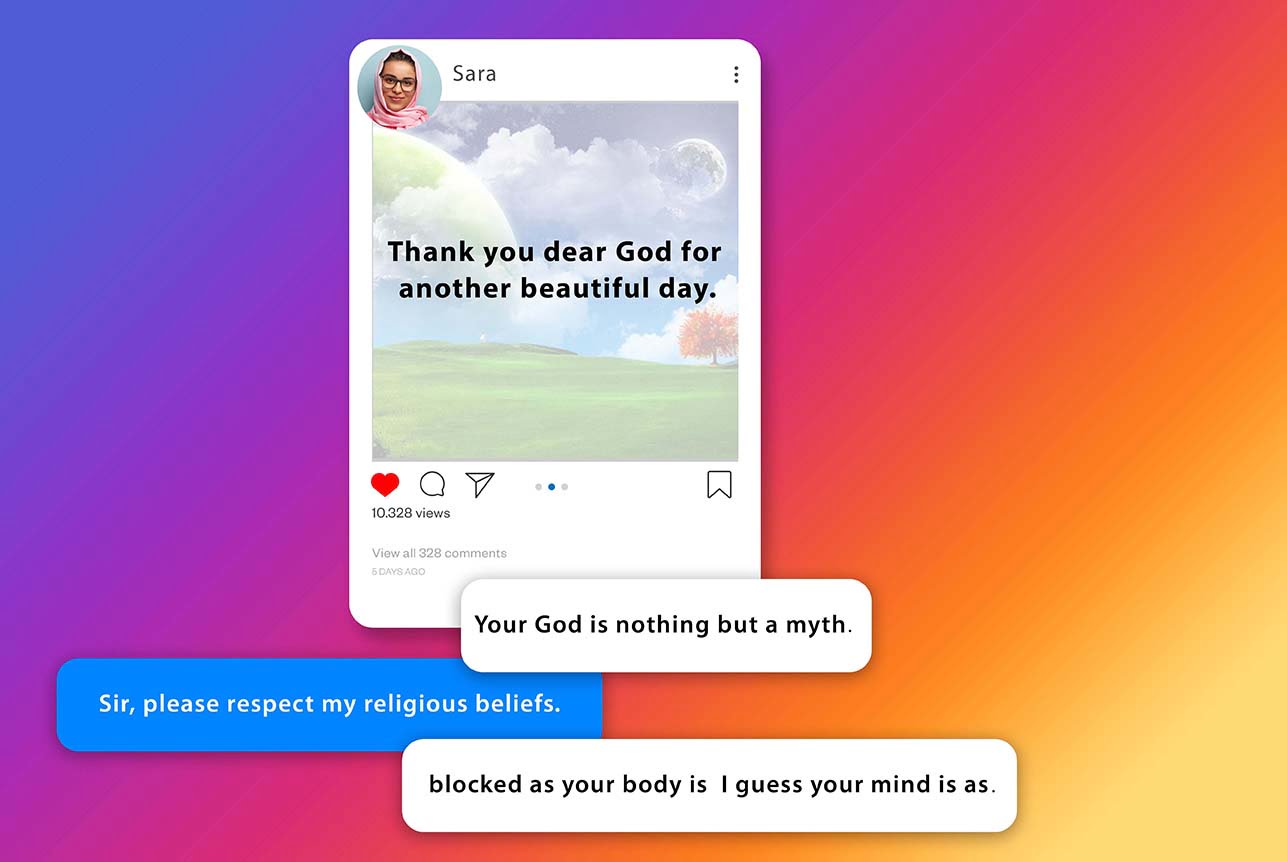
10. Flaming
Flaming constitutes directly sending insults to the victim or posting offensive things about them.
Unlike trolling, flaming is not a joke or an indirect insult. Bullies use profane language and offend their targets in a direct, open way, provoking an online fight.
11. Denigration
This type of online bullying is similar to dissing, only in this form, the cyberbully spreads baseless rumors or gossip to embarrass the victim and damage his reputation and relationships with other people. According to TeachThough: Most cyberbullying attacks take place through chatting and commenting on social media websites. Kids should be taught that if they wouldn’t say something to someone’s face, they shouldn’t say it to them online, through texting, or posting in any other way. But Digital Harassment is the perfect way for online aggressors to remain anonymous.
5 cyberbullying stories
Some people from different parts of the world have shared their experiences at the Cyberbullying Research Center.
Here are some of them:
A 13-year-old girl who surprisingly got called names like “Ugly Ragdoll” and “Useless” by her best friend.
A 21-year-old girl who ran out of ideas after stopping communication with a cyberbully who has been sending her mean tweets for weeks.
A mother who said her 16-year-old son had an acute psychotic break and was transferred to an adolescent psychiatric ward after being cyberbullied on Facebook for 8 hours.
A 15-year-old who’s been a victim of cyberbullying for FOUR YEARS. He has been receiving bashing messages on his birthdays.
A 22-year-old girls said her so-called “friends” made up sexually explicit content about her on MySpace.
In their own words, they said cyberbullying made them feel the following:

1. Lucy, a 10th-grader shared her story on Cybersmile:
There was a big party in Lucy’s town, but she couldn’t go. She then went on and shared a rude and angry post on her spam Instagram account, directed at those attending the event.
Her post got shared on Instagram and people started saying terrible things about her. So, she immediately apologized and made things right. For a while at least.
Some 6 months later, she posted a photo of herself and was met with dozens of mean comments. Her fellow 10th-graders and kids from other schools started attacking her. To make matters worse, no one defended her.
She told her parents and reported this incident to her school. After returning from a trip, she learned that the school had contacted the mother of the girl who was leading the comments about her.
The mother showed Lucy’s post and defended her daughter’s actions, responding that she said what she said because of that very post.
That is when Lucy realized that even though she was hurt, she had hurt the feelings of others on social media.
Although both girls were wrong to say those things, Lucy’s story reminds us that: once you post it, you can never take it back!
“Even though people forgive and forget, things stay on the internet forever and can come back to haunt you later in life.”
2. Young Roseanne told her story to ReachOut, an online mental health service in Australia:
Got cyberbullied by her friend. She wrote horrible things about her online. Since they were posted for the world to see, Roseanne felt like everybody was saying the same things.
She finally decided to physically distance herself from her cyberbully.
Bottled up with emotions, she kept it all to herself. But it got worse and she finally told someone. As she saw the positive reactions and support, she started telling more and more people.
I wish I had spoken to someone earlier; the more people I talked to, the easier it became.
3. A Ukrainian journalist who was studying at LSE told her story of identity theft; a form of cyberbullying.
One day, Valeria Kovtun received a message from one of her followers on Instagram, showing her a screenshot of a profile under a different name, but with her pictures and data!
Instagram removed the fake account shortly after Valeria reported it, but she was left scared by the thought of numerous fake accounts existing with her data on different platforms.
She was notified by Google and later by Facebook, that there were suspicious activities going on in her accounts. She panicked and tried to change her password, but the hacker was making it difficult for her.
Eventually, Facebook blocked her profile and luckily, Google identified the hack and let Valeria change her password. Even though she came out victorious, the fear remained…
She decided to make her accounts more secure by STAYING ALERT because as she says there is a lack of regulation on social media.
Even if the number of people who can view your posts is limited, your privacy is still at stake as you can hardly make sure everyone from your friend’s list is adhering to the code of ethics.
4. Kenneth Weishuhn’s tragic story on Family Orbit is a case of being attacked because of one’s sexual orientation, which should make parents more aware to protect their children:
14-year-old Kenneth’s classmates had created an anti-gay Facebook group and threatened to kill him.
But what had Kenneth done?
Kenneth had recently come out as gay. His own friends started making fun of him and left him feeling tormented and helpless.
He was harassed in school and online, to the point that he took his own life.
Sexual minorities are one of the most vulnerable groups to cyberbullying.
5. Amanda Tod’s devastating end was shared on the same site:
Amanda was approached by an unknown man and convinced her to send a nude picture of herself.
She was contacted again by the man on Facebook, threatening her to take part in a live sex show on camera, or he would share the nude photo with her friends.
Amanda refused, and her photo was released online. Unsurprisingly, she was contacted by bullies afterwards.
Even after moving to a new town, she couldn’t stop the cyberbullying.
Amanda attempted suicide two times, the second one being successful.
She was 15 years old.
That one instance led to a succession of cyberbullying and the threat of exposure.




